-
Posts
4,715 -
Joined
-
Last visited
-
Days Won
28
Content Type
Profiles
Forums
Blogs
Events
Resources
Videos
Link Directory
Downloads
Everything posted by Starbuck
-

Getting PopUps from watchtvnow.com
Starbuck replied to Skyclad's topic in Tech Support & Discussions Forum
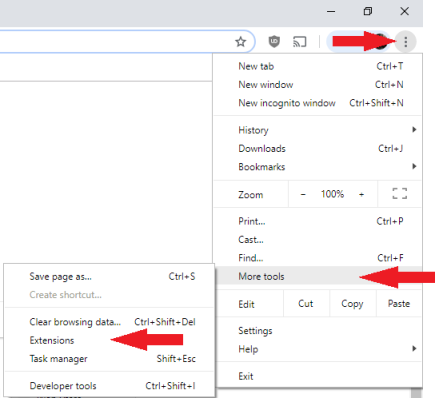
Hi Skyclad, Ok, according to the FRST report you use Chrome as your default browser. Have you tried running Firefox or IE to see if these popups still occur? If these popups only occur when the browser is running, there must be an extension or an addon that is causing it. Let's see if running Chrome in safe mode will put a stop to these. Running Chrome in safe mode will disable all add-ons & extensions. Click the Menu button in the top-right corner of the window Select More Tools and then Extensions. Uncheck all the Enabled check boxes and restart the browser. If this stops the popups..... you will need to enable the extensions one at a time until you find the one that is causing the problem. Let me know how this goes, also if the problem occurs when using Firefox or IE. -

Getting PopUps from watchtvnow.com
Starbuck replied to Skyclad's topic in Tech Support & Discussions Forum
Hi Skyclad, Do you get these popups when running your browser, or do they also happen when the system is not on the internet? -

Getting PopUps from watchtvnow.com
Starbuck replied to Skyclad's topic in Tech Support & Discussions Forum
Yes that sounds good, give it a couple of days and then let me know the outcome. -

Getting PopUps from watchtvnow.com
Starbuck replied to Skyclad's topic in Tech Support & Discussions Forum
Hi Skyclad, The reports look ok. Are you still getting the popups from 'watchtvnow' ? -

Getting PopUps from watchtvnow.com
Starbuck replied to Skyclad's topic in Tech Support & Discussions Forum
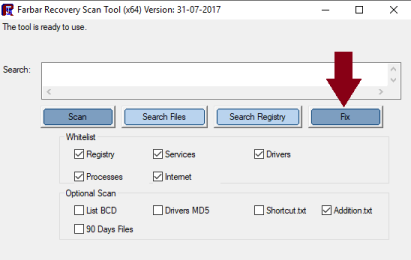
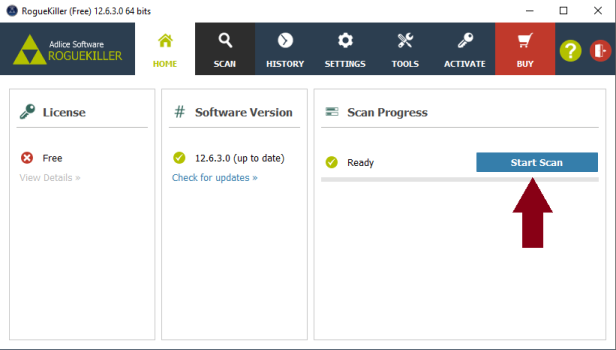
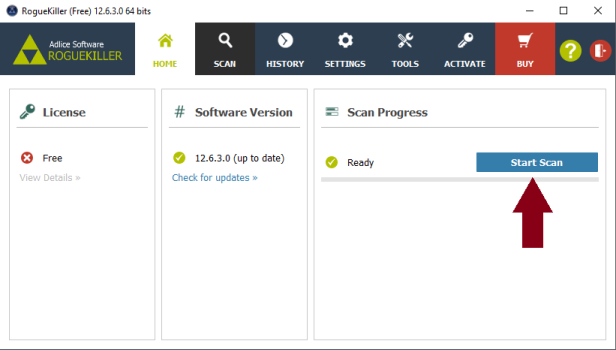
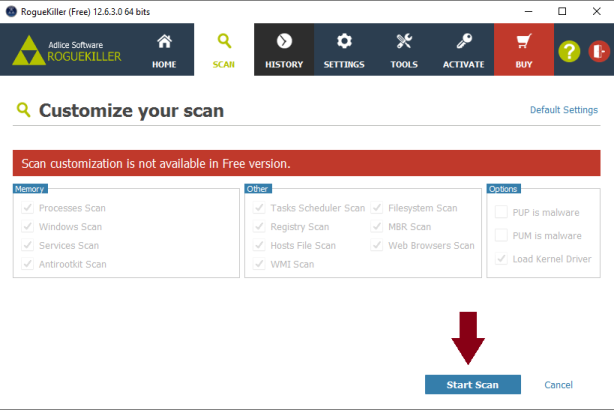
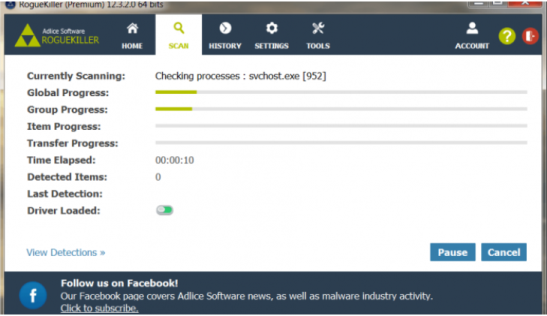
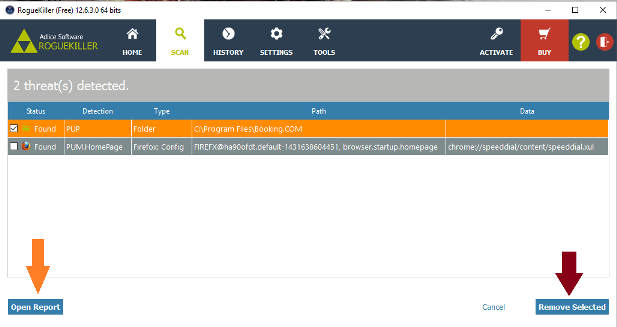
Hi Skyclad, I added the reports to your post because they're a lot easier to read and check that way. Step 1 Please download the attached fixlist.txt file (bottom of this post) and save it to C:\Users\Mike\Downloads . NOTE. It's important that both files, FRST and fixlist.txt are in the same location or the fix will not work. NOTICE: This script was written specifically for this user, for use on that particular machine. Running this on another machine may cause damage to your operating system Re-run FRST/FRST64 (which ever is installed ) and press the Fix button just once and wait. The tool will make a log in Download folder (Fixlog.txt). Please post this in your next reply. Step 2 Please reset all browsers to their original settings. To Reset Firefox At the top of the Firefox window, click the Help menu and select Troubleshooting Information Click the Reset Firefox… button in the upper-right corner of the Troubleshooting Information page. To continue, click Reset Firefox in the confirmation window that opens. Firefox will close and be reset. When it's done, a window will list the information that was imported. Click Finish and Firefox will open. Note: After the reset is finished, your old Firefox profile information will be placed on your desktop in a folder named "Old Firefox Data." If the reset didn't fix your problem you can restore some of the information not saved by copying files to the new profile that was created. If you don't need this folder any longer, you should delete it as it contains sensitive information. The reset feature works by creating a new profile folder for you while saving your most important data. Firefox will try to keep the following data: Bookmarks Browsing history Passwords Cookies Web form auto-fill information Personal dictionary -------------------- Reset IE back to the defaults. Close any Internet Explorer or Windows Explorer windows that are currently open. Open Internet Explorer by clicking the Start button, and then clicking Internet Explorer. Click the Tools button, and then click Internet Options. Click the Advanced tab, and then click Reset. Select the Delete personal settings check box if you would like to remove browsing history, search providers, Accelerators, home pages, and InPrivate Filtering data. In the Reset Internet Explorer Settings dialog box, click Reset. When Internet Explorer finishes applying default settings, click Close, and then click OK. Close Internet Explorer. Your changes will take effect the next time you open Internet Explorer. ----------------- To reset Google Chrome Click the Menu option button at the top right of the Google Chrome screen Select Settings. Click Show advanced settings and find the "Reset browser settings” section. Click Reset browser settings. In the dialogue that appears, click Reset. Note: When the "Help make Google Chrome better by reporting the current settings" tick box is selected you are anonymously sending Google your Chrome settings. Reporting these settings allows us to analyse trends and work to prevent future unwanted settings changes. Resetting your browser settings will impact the settings below: Default search engine and saved search engines will be reset and to their original defaults. Homepage button will be hidden and the URL that you previously set will be removed. Default startup tabs will be cleared. The browser will show a new tab when you startup or continue where you left off if you're on a Chromebook. New Tab page will be empty unless you have a version of Chrome with an extension that controls it. In that case your page may be preserved. Pinned tabs will be unpinned. Content settings will be cleared and reset to their installation defaults. Cookies and site data will be cleared. Extensions and themes will be disabled. Step 3 Please download RogueKiller Anti-malware (Free) onto your desktop. Close all open programs and internet browsers. Double click on RogueKiller Anti-malware to install the tool. Vista/Windows 7/8/10 users right-click and select Run As Administrator. Select Accept the User Agreement then continue to click Next then finally click Install Click Finish . When the program opens..... click Scan Click Start Scan Double check anything found and tick to select items to be removed Click Remove Selected When the items have been removed.... Click Open Report >> Open TXT. Copy and paste that report into your next reply. In your next reply, please submit: Fixlog.txt RogueKiller report Also give me an update on the system. Thanks. fixlist.txt -

Getting PopUps from watchtvnow.com
Starbuck replied to Skyclad's topic in Tech Support & Discussions Forum
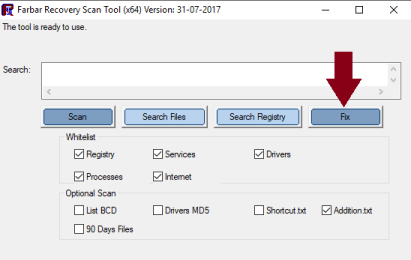
Hi Skyclad, I'm sure we can sort this out for you. Please download the following program and post the 2 reports asked for. Note: There are both 32-bit and 64-bit versions of Farbar Recovery Scan Tool available. Please pick the version that matches your operating system's bit type. If you are unsure what you're system bit type is..... click Here for help. For x32 bit systems download Farbar Recovery Scan Tool and save it to your Desktop. For x64 bit systems download Farbar Recovery Scan Tool x64 and save it to your Desktop. Double-click the downloaded icon to run the tool. Vista/Windows 7/8/10 users right-click and select Run As Administrator When the tool opens click Yes to disclaimer. Make sure that Addition.txt is selected at the bottom Press Scan button. It will make a log (FRST.txt) in the same directory the tool is run. Please copy and paste it to your reply. When the tool is run, it also makes another log (Addition.txt). Please copy and paste it to your reply also. Thanks -
Sorry to say, but 2019 has not ushered in new “tips to bypass FB” as it supposedly limits posts on your news feed. Nor has Facebook ushered in a new algorithm that “chooses the same few people – about 25 – who will read your posts”, at least not that we’ve heard. Rather, we’re still stuck with whatever murky, stubbornly unfathomable algorithms Facebook uses to determine the order of content in our feeds, regardless of what the latest, breathless spin on this wheezy old hoax wants you to believe. To wit: The last time we wrestled with this particular pudding was back in February when Snopes debunked the viral hoax and said no, a new Facebook algorithm will NOT only show you 26 friends. Snopes pointed out at the time that the algorithm hoax followed on the heels of a real Facebook announcement from 11 January 2018 about a major overhaul in how newsfeed works. It wasn’t about squeezing out your friends, though. In fact, Facebook had the opposite in mind: it said it was working on turning the tables when it comes to personal content from friends and family making way for an explosion of corporate posts, be they from corporations, businesses or media. Snopes contacted Facebook to ask whether the claim of limiting personal interactions had merit. A representative said no, it does not. Why is the rumor, then, still lying its way to the top of newsfeeds? By convincing a user to copy and paste, rather than share the post, it’s much harder to shut it down. The best thing you can do is carefully sidestep this cow patty. You can also do us all a solid by warning your friends not to perpetuate the spread of fake news posts. Source: Warn your friends they can’t bypass Facebook with this hoax
-
-
Hi joddle, Sorry for the late reply, I've been laid up with the flu for the last few days. Reformatting the router should remove it, but there is a removal process that might be worth running through. Remove the Photo.scr Monero Miner The link will also explain a bit more about the infection. Let me know how it goes and if you find anything else. We can always look into things a bit more if there are still traces.
-
Sorry but I have to ask.....WHY? Windows XP was released in 2001. Extended support for Windows XP ended on April 8, 2014. Windows XP is remotely exploitable by numerous security holes that were discovered after Microsoft stopped supporting it. It's not a system that can be used safely. Is it still safe to use Windows XP? It belongs on the Antiques Roadshow.
-

How do I set another image program in w10
Starbuck replied to mij's topic in Tech Support & Discussions Forum
That is one piece of software that I have no knowledge of at all. -

How do I set another image program in w10
Starbuck replied to mij's topic in Tech Support & Discussions Forum
What picture/photo software are you now using? -

How do I set another image program in w10
Starbuck replied to mij's topic in Tech Support & Discussions Forum
Hi Jim I can understand your frustration ....... this is a common problem with Win 10. There's only one way that has worked for me...... I take it you have your preferred picture/photo software installed? Click Start >> Settings >> Apps >> Default Apps Ignore the normal way of changing the default app (which doesn't work anyway) Scroll down to the bottom of the page and click on Set Defaults by App. From the list of installed Apps, select your preferred picture/photo software program. Then click Manage when the box opens. When the list of file types opens..... You'll have to manually change the photo/picture file types one at a time (jpg, jpeg etc ) from the Microsoft default to your preferred default. Click on the program listed as default .... a list will open. Select your preferred program. The default program should now change. This is the only way that's worked for me. -
Traditional antivirus software has a tough time detecting malware used in the campaign. A new, active campaign is using malware capable of dancing around traditional antivirus solutions in order to empty cryptocurrency wallets. The malware is being used in the DarkGate campaign, a previously undetected hacking operation uncovered this week by enSilo security researchers. According to the team, DarkGate is currently underway in Spain and France, targeting Microsoft Windows PCs by way of torrent files. Torrent files are most commonly associated with pirated content, but the technology itself is not illegal and can be used by consumers and businesses alike to share files of large sizes. In this case, however, the infected .torrent files masquerade as pirated versions of popular television shows and films including The Walking Dead. The DarkGate malware uses a variety of obfuscation techniques to circumvent traditional antivirus solutions. The malware's command-and-control (C2) structure, which allows operators to send commands remotely and for the malware to transfer stolen data, is cloaked in DNS records from legitimate services including Akamai CDN and AWS. By hiding the C2 under the skirts of reputable DNS services, this allows the malware to pass a reputation check when it comes to shady services or bulletproof hosting platforms which have become associated with malware and criminal campaigns. In addition, DarkGate uses vendor-based checks and actions, including a method known as "process hollowing" to avoid detection by AV software. This technique requires a legitimate software program to be loaded in a suspended state -- but only to act as a container for malicious processes which are then able to operate instead of the trustworthy program. DarkGate will also perform a number of checks in an attempt to ascertain whether or not it has landed in a sandbox environment -- used by researchers to analyze and unpack malicious software -- and will perform a scan for common AV systems, such as Avast, Bitdefender, Trend Micro, and Kaspersky. The malware also makes use of recovery tools to prevent files critical to its operation from being deleted. enSilo says that the malware author "invested significant time and effort into remaining undetected," and during testing, it was found that "most AV vendors failed to detect it." When executed, DarkGate implements two User Account Control (UAC) bypass techniques in order to gain system privileges, download, and execute a range of additional malware payloads. These packages give DarkGate the ability to steal credentials associated with a victim's cryptocurrency wallets, execute ransomware payloads, create a remote access tunnel for operators to hijack the system, and also implement covert cryptocurrency mining operations. According to enSilo, the C2 is overseen by human operators who act when they are alerted to new infections related to cryptocurrency wallets by installing the remote access tools necessary to compromise virtual coin funds. Source: Most antivirus programs fail to detect this cryptocurrency-stealing malware | ZDNet
-
Hi Bringe, Nothing stupid about not knowing something .... we've all been there. See if this helps. For Win XP, you simply need to open Command Prompt to access diskpart: Click >> Start Click >> Run Type in >> cmd Press Enter key or click OK At the Command Prompt window, type in diskpart Press Enter Accessing Diskpart on Win 7 is slightly different.
-
No problem at all. Funny you should say that .... I leave in a few hours lol. Let's finish the cleaning process and remove the tools we have used. Step 1 FRST can now be removed: Right click on the FRST icon and select delete. Right click on any fixlog.txt or fixlist.txt files and select delete. Navigate to: C:\frst and delete the frst folder Step 2 RogueKiller AntiMalware can be removed using the add/Remove Programs feature in Control Panel. Step 3 To remove AdwCleaner Restart AdwCleaner ... click on the Uninstall button from the main screen. This will remove all the files created and the program. Step 4 Eset can be removed using the add/Remove Programs feature in Control Panel. Glad I was able to help. Safe surfing.
-
Seems that Eset did get those last 2 entries: So everything malicious that can be seen, has now been removed. Give the system awhile to run and if nothing untoward is thrown up I'll finish off tomorrow evening.
-
Ok, that's good. Sorry I missed those entries earlier. Let's see if Eset finds anything.
-
Have just double checked the FRST report and have noticed that I've missed a few leftover entries for Norton AV. These should be removed. Please download the attached fixlist.txt file (bottom of this post) and save it to the Desktop. NOTE. It's important that both files, FRST and fixlist.txt are in the same location or the fix will not work. NOTICE: This script was written specifically for this user, for use on that particular machine. Running this on another machine may cause damage to your operating system Re-run FRST/FRST64 (which ever is installed ) and press the Fix button just once and wait. The tool will make a log on the Desktop (Fixlog.txt). Please post this in your next reply. fixlist.txt
-
Hi Rustys, The FRST fix did it's job. :) Looking a lot better now. You might want to look into this.... Click Start... Control Panel Then click on the Security button. Under Windows Firewall... click on Turn Windows Firewall on or off. Make sure the ON (recommended) is selected.... then click Apply and Ok. Let's run a double check on things now. I'd like us to scan your machine with ESET OnlineScan This process may may take several hours, that is normal. Download esetsmartinstaller_enu.exe and save it to your Desktop Double click the icon Check YES, I accept the Terms of Use Click the Start button Accept any security warnings from your browser Click Advanced settings Check the following items Enable detection of potentially unwanted applications Remove found threats Scan archives Scan for potentially unsafe applications Enable Anti-Stealth technology Click Start ESET will then download updates and begin scanning your computer If no threats are found simply click Uninstall application on close and hit Finish If threats are found click List of found threats Click Export to text file Save the file on your Desktop as ESET.txt Click Back Click Finish Close the ESET Online Scanner window Copy and paste the contents of ESET.txt in your next reply
-
Hi Rustys, Looks like Rogue Killer has cleaned up quite a bit for us. Let's deal with a few more items now. Please download the attached fixlist.txt file (bottom of this post) and save it to the Desktop. NOTE. It's important that both files, FRST and fixlist.txt are in the same location or the fix will not work. NOTICE: This script was written specifically for this user, for use on that particular machine. Running this on another machine may cause damage to your operating system Re-run FRST/FRST64 (which ever is installed ) and press the Fix button just once and wait. The tool will make a log on the Desktop (Fixlog.txt). Please post this in your next reply. In your next reply, also give me an update on how the system is running now. Thanks fixlist.txt
-
Yes, move on to the next steps.
-
Nice one
-
Hi Rustys, You've got a good one there lol. It's been well and truly abused. First thing to do is to set the clock. Both FRST and AdwCleaner are both showing: Scan result of Farbar Recovery Scan Tool (FRST) (x86) Version: 24.10.2018 Ran by Angela (administrator) on ANGELA-PC (20-03-2007 01:02:34) ----------------- Malwarebytes AdwCleaner 7.2.4.0 # ------------------------------- # Build: 09-25-2018 # Database: 2018-09-21.1 (Local) # Support: Customer Support & Help Center # # ------------------------------- # Mode: Clean # ------------------------------- # Start: 03-20-2007 Before trying to clean up the report, we need to hit this system with something a bit harder than AdwCleaner. Step 1 Please uninstall the following program: Step 2 Please download RogueKiller Anti-malware (Free) onto your desktop. Close all open programs and internet browsers. Double click on RogueKiller Anti-malware to install the tool. Vista/Windows 7/8/10 users right-click and select Run As Administrator. Select Accept the User Agreement then continue to click Next then finally click Install Click Finish . When the program opens..... click Scan Click Start Scan Double check anything found and tick to select items to be removed Click Remove Selected When the items have been removed.... Click Open Report >> Open TXT. Copy and paste that report into your next reply. Step 3 Re-run FRST and let me have a fresh set of reports ( after running Rogue Killer) In your next reply, please submit: Rogue Killer report Fresh set of FRST reports. Thanks.
-
Glad everything seems fine again now.