-
Posts
4,715 -
Joined
-
Last visited
-
Days Won
28
Content Type
Profiles
Forums
Blogs
Events
Resources
Videos
Link Directory
Downloads
Everything posted by Starbuck
-
Believe it or not, some hardy souls are still running Windows 7 on PCs equipped with turn-of-the-century Pentium III CPUs. But the latest round of Windows 7 security patches won't install on those devices. Here's the background. In August 2000, nearly 18 years ago, Intel proudly showed off its newest CPU family, the Pentium 4. ZDNet was there to cover the announcement and highlighted one of the signature features of the new chip: I'm old enough to remember that announcement, and yes, the addition of support for Streaming SIMD Extensions 2 (SSE2) was a big deal at the time. It was a high-end feature in 2000, but by 2004 or so every mainstream processor supported this feature. The CPU in your more modern PC almost certainly supports a later version; the latest and greatest release is SSE 4.2. The point is, if you're running a PC today, in mid-2018, that doesn't support SSE2, you should be charging admission to your computer museum. You probably upgraded it from Windows 98 to Windows XP and then to Windows 7, and you've been humming along for nearly two decades, which is impressive. SSE2 support became a big deal in 2012, when Microsoft announced that it was one of three mandatory CPU features required for its new OS. Windows 10 has the same requirements. That was six years ago, an eternity in computing terms, so imagine my surprise when the subject came up again just last week, this time in the context of Windows 7. The problem began with the March 2018 monthly security update for Windows 7 (KB4088875), which included this warning under the "Known issues" heading: As my erstwhile coauthor and longtime friend Woody Leonhard noted in his wrap-up of the issue, the text alongside that issue, under the column labeled "Workaround," has changed over the past three months. Initially, it said, "Microsoft is working on a resolution and will provide an update in an upcoming release." But in the latest (June) update, the text now reads: "Upgrade your machines with a processor that supports SSE2 or virtualize those machines." Is this a violation of Microsoft's support commitment to its customers using Windows 7? Not under the terms of the Microsoft Business, Developer and Desktop Operating Systems Policy, which anticipates this very situation: And that's exactly what appears to have happened here. Beginning with the March update, those cumulative Windows 7 patches won't install on a Pentium III system. Microsoft hasn't disclosed the reason behind that incompatibility, but you don't need much of an imagination to figure that the problem is probably related to the Spectre and Meltdown vulnerabilities, which affect two decades' worth of Intel CPUs. I've asked Microsoft for further details, and I expect a vigorous "No comment." (On the off chance that they surprise me, I will update this post.) But even without their comment I can surmise that the massive changes required by the Meltdown/Spectre patches were too much for the Pentium III family to handle, and so those machines reached the end of the Windows 7 support cycle about 18 months earlier than their younger brethren. Does Microsoft have a responsibility to support ancient CPU architectures like this? I have a hard time summoning much sympathy for anyone who has managed to squeeze 18 years of life from a PC and can probably replace it with one that is 20 times more powerful at about 20 percent of the price. Source: Microsoft unexpectedly drops Windows 7 support for some ancient CPUs | ZDNet
-
Very sorry to hear that Bob. My condolences to you and your friends family.
-
The intentions of and delivery method of Mylobot are unknown - but it appears to be the work of a sophisticated attacker who could deliver trojans, ransomware and more. A new malware campaign is roping systems into a botnet and providing the attackers with complete control over infected victims, plus the ability to deliver additional payloads, putting the victims' devices at risk of Trojans, keyloggers, DDoS attacks and other malicious schemes. The malware comes equipped with three different layers of evasion techniques which have been described by the researchers at Deep Instinct who uncovered the malware as complex, rare and "never seen in the wild before". Dubbed Mylobot after a researcher's pet dog, the origins of the malware and its delivery method are currently unknown, but it appears to have a connection to Locky ransomware -- one of the most prolific forms of malware during last year. The sophisticated nature of the botnet suggests that those behind it aren't amateurs, with Mylobot incorporating various techniques to avoid detection. They include anti-sandboxing, anti-debugging, encrypted files and reflective EXE, which is the ability to execute EXE files directly from memory without having them on the disk. The technique is not common and was only uncovered in 2016, and makes the malware ever harder to detect and trace. On top of this, Mylobot incorporates a delaying mechanism which waits for two weeks before making contact with the attacker's command and control servers -- another means of avoiding detection. "The reason to do 14 days of sleep is to avoid any network and malicious activity, thus bypassing cyber security solutions like endpoint detection and response, threat hunting and sandboxing," Tom Nipravsky, Deep Instinct security researcher told ZDNet. Once installed on a system Mylobot shuts down Windows Defender and Windows Update, while also blocking additional ports on the firewall -- all tactics to ensure that its malicious activity can operate without being impeded. In addition to this, it actively targets and deletes any other instances of malware which have previously been installed on the machine, even specifically aiming for other botnets. The thinking behind this is simple -- eliminating the competition in order to ensure the attackers gain control over the largest network of infected computers to make the most profit from abusing the compromised machines as possible. Once a computer is part of the botnet, the attacker can take complete control of the system and further payloads and instructions can be delivered from the command and control server. "The expected damage here depends on the payload the attacker decides to distribute. It can vary from downloading and executing ransomware and banking trojans, among others," said Nipravsky. "This can result in loss of tremendous amount of data, the need to shut down computers for recovery purposes, which can lead to disasters in the enterprise." Researchers haven't detailed what additional payloads are being downloaded, but analysis of the command and control domains related to Mylobot uncovered connections to Locky ransomware and other malware. "According to our research, the IP of the C&C server was first seen on November 2015, and is linked to DorkBot, Locky and Ramdo," Nipravsky said. With the C&C having been active for two and a half years, it indicates those behind Mylobot have been active for some time -- and they use tactics which suggest a well-resourced operation. "The botnet is trying to connect to 1,404 different domains -- at the time of writing this research, only one was alive. This is an indication for big resources in order to register all those domains," said Nipravsky. The malware isn't widespread and it still remains unclear who the attacker behind Mylobot is, how the malware is delivered or even what their ultimate goal is -- but one thing researchers have concluded from the complexity of the scheme is that it isn't an amateur operation. "We haven't found any indication about who the author is, but based on the code, this is someone who knows what they're doing," said Nipravsky. Source: This new Windows malware wants to add your PC to a botnet - or worse | ZDNet
-

Office update deletes Word
Starbuck replied to RustyKnight's topic in Tech Support & Discussions Forum
Is this a Win 10 operating system? Win10 is known to remove old programs during a major update. Windows may remove programs during an update for compatibility reasons. If a program is known to cause crashes, bugs, or otherwise conflict with Windows, Windows may remove it to keep your system stable. Windows doesn’t provide any notice that it’s removed a program – the program will just appear to vanish from your system. As Microsoft discontinued 'Works' in 2009 it's a good bet that it's not stable with the latest Win10 updates. The Microsoft Services Agreement that applies to Windows does explicitly state that Microsoft may remove access to software or hardware. -
Researchers uncover a form of malware that's still in development - but it has the potential to become a nasty threat. An experimental form of Android malware delivers a banking trojan, a keylogger and ransomware to those unfortunate to fall victim to it. Uncovered by security researchers at security company ThreatFabric, the malware was first thought to be an updated version of Lokibot - but as it contain various new features researchers are labelling it as a new form of malware - MysteryBot. However, MysteryBot and LokiBot share the same command and control server, indicating a strong link between the two forms malware, with the potential that they've been developed by the same attacker. The malware is also potentially potent, with the trojan capable of controlling the functionality of the infected devices, including the ability to read messages, gather contact information and more. There are also commands for stealing emails and remotely starting applications, but these particular tools don't appear to be active yet, suggesting that this malware is still in the development phase. While many Android malware families concentrate on attacking older versions of the Google operating system, MysteryBot has the capability to actively target Android versions 7 and 8 using overlay screens designed to look like real bank websites, but are in fact run by the attackers, the researchers said. Fake websites of a wide variety of banks across the world are able to be displayed to the victim, ensuring that the attackers can cast a wide net for stealing entered credentials. Once active on the device, the malware is listed as a fake version of Adobe Flash Player. However, researchers haven't detailed how the payload is initially delivered onto the device. Researchers say that the way the malware records keylogging in an innovative new way, by determining which key has been pressed by its location on the screen in relation to others, something it can do when the keyboard is held both horizontally and vertically, the researchers explain in a blog post. However, as with other features of the malware, the keylogger still appears to be in development as there's currently no way for the logged keys to be stored on the command server. On top of the ability to infect victims with a trojan and a keylogger, those behind MysteryBot have also been experimenting with a ransomware tool. The embedded ransomware feature enables the malware to individually encrypt files and store them in a passworded ZIP archive. When the encryption is complete, a message accuses the victim of having watched adult content and demands that an email address be contacted to gain a password - and presumably pay for the privilege. However, the ransomware element of MysteryBot doesn't appear to be sophisticated. Not only because it requires contact via email, but that the password is only eight characters long, which in theory could be guessed by brute-force. Secondly, victims are assigned an ID between 0 and 9999 and since there's no verification of existing ID, it's possible the attackers could duplicate the Ids and make it impossible for victims to retrieve files. But despite some of the capabilities of MysteryBot currently being underdeveloped, the malware is still a potential threat. "The enhanced overlay attacks also running on the latest Android versions combined with advanced keylogging and the potential under-development features will allow MysteryBot to harvest a broad set of personal identifiable information in order to perform fraud," wrote researchers. MysteryBot isn't currently widespread and is still under development, but users should be wary of any applications they download which ask for an excessive number of permissions. Source: This new Android malware delivers banking trojan, keylogger and ransomware | ZDNet
-
Over the weekend, Microsoft announced that starting on July 1st 2018 they are no longer offering support for Windows 7, Windows 8, Windows 8.1, and a wide variety of older applications in the Microsoft Community forums. This does not mean that volunteers will not be able to answer questions, only that Microsoft staff themselves will no longer respond to them. The announcement posted to the Microsoft Community forums states: As you can see all of the products mentioned are old with mainstream support already ended. Therefore, it does not come as a surprise to see Microsoft assigning their staff to responding to questions for newer products that are still under full support. Source: Microsoft Ending Support for Windows 7, 8, & Older Apps in the Microsoft Forums
-
Thanks Bob. No problems now.
-
The announcement comes just six months after Yahoo and AOL parent company Oath discontinued AIM. If you're interested in downloading your Yahoo Messenger chat history, be sure to do that soon. Pour one out for Yahoo Messenger. Yahoo has announced plans to discontinue the vintage chat service on July 17, 2018. "We know we have many loyal fans who have used Yahoo Messenger since its beginning as one of the first chat apps of its kind," the company wrote. "As the communications landscape continues to change over, we're focusing on building and introducing new, exciting communications tools that better fit consumer needs." Yahoo first introduced the chat service in 1998, a year after the now-defunct AOL Instant Messenger (otherwise known as AIM) made its debut. The company originally called the service Pager, but in 1999 rebranded it to Messenger. Under former CEO Marissa Mayer, Yahoo in 2015 launched a new version of Messenger with features like bulk photo sharing, easy access to GIFs, and a Snapchat-esque remote delete function. But trying to compete for users in a crowded market dominated by modern apps like WhatsApp, Facebook Messenger, Skype, Viber, Snapchat, Line, and Telegram proved difficult. The revamped version of Messenger never really caught on with the masses. Now, Messenger will only continue working normally until July 17. After that date, you will no longer be able to access your chats and the service won't work. Your Yahoo ID will continue to work for other Yahoo properties like Mail and Fantasy. You have six months to download your Messenger chat history, if you want it. To do that, head over to Yahoo's downloader request site, sign in, select a verification method, enter the code sent to you, click Download, and enter an email where you want the file sent. In its announcement, Yahoo said it doesn't have an immediate replacement product for Messenger, but is working on a group messaging app called Squirrel, which is currently in beta and only available to those with an invitation. If you're interested in trying out Squirrel, you can head here to request an invite. Source: Yahoo Messenger to Be Discontinued July 17
-

announcement Site Upgraded - Now Fully GDPR Compliant
Starbuck replied to AWS's topic in Tech Support & Discussions Forum
Noted. -
Hi joddle, There is a very detailed tutorial here: How to set up file sharing in Windows 10 Take a look and see if there's something that you may have missed.
-
Google’s in trouble again over the “Safari Workaround”: the iPhone shakedown for personal information from millions of iPhone users. In 2012, the workaround got the search giant fined by the US Federal Trade Commission (FTC) for $22.5m, fined again a year later for $17m after it got sued by dozens of states, and now has the UK’s Google You Owe Us campaign out for its own pound of flesh. Make that a few pounds of flesh: The Google You Owe Us campaign has started the process of getting its own comeuppance, and the US fines pale in comparison to what the British group is after. Monday marked day one in London’s high court, where the collective action is suing the company for what could be as much as £3.2bn (USD $4.3b), according to court filings. It alleges “clandestine tracking and collation” of information that included race, physical and mental health, political leanings, sexuality, social class, financial data, shopping habits and location data. On the campaign’s site, it alleges that Google’s Safari Workaround tracked iPhone users’ internet browsing history, which Google then used to sell a targeted advertising service. Google You Owe Us first launched a “representative action” (similar to a class action in the US) in November 2017. The action alleges that the search giant: On Monday, Google You Owe Us lawyers told the high court that Google collected personal information from 4.4 million iPhone users in the UK. Richard Lloyd, former director of the UK consumer champion Which?, is heading up the collective action. His lawyer, Hugh Tomlinson QC, told the court that Google bypassed the privacy settings of Apple’s Safari browser on iPhones between August 2011 and February 2012 in order to divide people into categories so as to target marketing at them. For this purpose, Google allegedly aggregated the data and shuffled users into groups for targeted marketing that included categories such as “football lovers” or “current affairs enthusiasts.” Bloomberg reports that if the group action has its way in court, each affected iPhone user could receive £750 (approx. $1,000). Google You Owe Us says don’t worry about whether you’re part of the claim: just sit back and let Richard Lloyd and the lawyers take care of the case. To see if you were affected by Google’s actions, or if you don’t want to be part of the claim, you can read more on the group’s FAQ page. Google has said that there’s no evidence that the Safari Workaround resulted in any information being disclosed to third parties; that it’s impossible to identify those who may have been affected; that the claim’s got no chance of success; and that the claim relates to events that are six years old and which have already been addressed. Source: Google in court over ‘clandestine tracking’ of 4.4m iPhone users
-
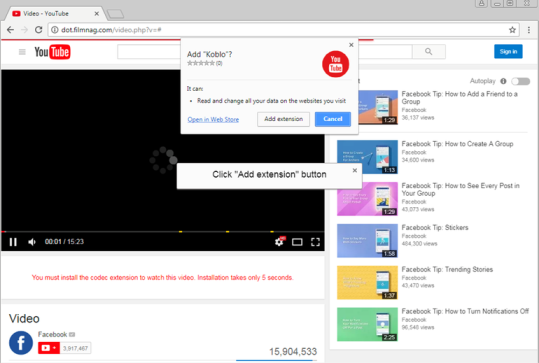
A spike infections follows an update to the password and cryptocurrency-stealing malware. A form of malware which uses fake Facebook Messenger messages to spread has suddenly surged back into life and has developed new tricks to steal passwords, steal cryptocurrency and engage in cryptojacking. First uncovered in August last year, the malware used phishing messages over Facebook Messenger to direct victims to fake versions of websites like YouTube, at which point they are encouraged to download a malicious Chrome extension. The malware has remained under the radar since then, at least until April when it appears to have suddenly spiked in activity, targeting Facebook users around the world. Analysis by researchers at security company Trend Micro - which has dubbed the malware FacexWorm - said that while the malicious software is still spread via Facebook and exploits Google Chrome, many of its capabilities have been completely reworked. New abilities include the capability to steal account credentials from selected websites, such as Google as well as cryptocurrency websites. It also pushes cryptocurrency scams of its own and mines infected systems for additional currency. But in order to conduct any of this activity, the malware needs to be installed on the system of a victim. Victims received a link out of the blue from a Facebook contact which directs them to a fake YouTube page. This page asks the victim to install a codec extension to play the video. If run, this extension will install FacexWorm, which asks for permissions to access the site and change data. This worm enables contact with the command and control server to access Facebook. This connection results in more fake YouTube links being sent to contacts to continue the spread of the malware. Researchers note that if the link is sent to a user who isn't using Google Chrome, the link diverts to a random advert - perhaps a remnant of the original function of the malware. FacexWorm itself is a clone of a normal Google Chrome extension, but injected with malicious code. This is delivered by downloading additional JavaScript code each time the browser is opened and whenever a new website is opened. If the malware is coded to retrieve credentials from that site, it retrieves additional Javascript in order to execute additional behaviours, which include stealing login credentials. In addition to this, the malware targets those using cryptocurrency trading platforms by searching for keywords like 'blockchain' and 'etherium' in the URL. If this is detected, FacexWorm sends users to a scam webpage which asks the user to send anywhere between 0.5 and 10 of the Ether cryptocurrency for 'wallet address verification' with a promise it will send more back. Obviously, if a user does this, they'll get nothing back at all - fortunately, researchers say nobody has sent money to the address. However, the attackers also attempt to maliciously earn cryptocurrency via other means, including the use of attacker-controlled referral links which provide them with some income each time users buy currency via the link. FacexWorm also injects the victim with a cryptocurrency miner. Researchers say the miner uses just 20 percent of the infected system's CPU, a tactic likely adopted to ensure the miner isn't discovered. But the malware does contain a mechanism to keep itself hidden; if the extension management tab is opened, FacexWorm will immediately close it, a protection method also used by malicious extensions such as DroidClub. While Trend Micro says malicious extensions are quickly removed from the Chrome Web Store, the attackers are quick to re-upload them. ZDNet has contacted Google, but hadn't received a response at the time of writing. Facebook is aware of the malware and said that Messenger can stop the spread of malicious links. "We maintain a number of automated systems to help stop harmful links and files from appearing on Facebook and in Messenger. If we suspect your computer is infected with malware, we will provide you with a free anti-virus scan from our trusted partners," the company said in a statement. In order to avoid becoming infected in the first place, Trend Micro warns users to: "Think before sharing, be more prudent against unsolicited or suspicious messages, and enable tighter privacy settings for your social media accounts." Source: This password-stealing malware uses Facebook Messenger to spread further | ZDNet
-
Company winding down development, report claims Microsoft has been very committed to offering Windows 10 with a pre-installed set of core apps for the essential activities that users typically perform every day, but as the company is reorganizing its business, plans for the future of Windows are also being updated. As a result, one change that Windows 10 could undergo would be the retirement of some Windows 10 apps, with a report claiming that Microsoft is already winding down development of several included applications. Thurrott writes that stocks and weather apps coming with Windows 10 could be the first victims, though there might be several other names on Microsoft’s blacklist, including Mail and Calendar. On the other hand, it’s not known if these could get the ax as well because they “have a higher priority because of their usage,” the report says. Edge team expanding Engineers working on the apps that are supposed to be impacted by these changes are moving to the Edge team, as Microsoft is more committed to improving the browser in Redstone 5. At the same time, the Edge development team is also getting more members from other units of the Windows group as Microsoft has canceled several Redstone 5 features, and engineers are being transitioned to the browser instead, the report adds. Microsoft will pay more focus to enterprise features in the coming years, and these internal changes show that Redstone 5 due in the fall could be the first to more strongly push Windows into this direction. And while apps like stocks and weather might be retired, Microsoft is investing aggressively in PWA apps, which could help the company address the lack of apps in the Store in an easier and more effective manner. At this point, there are only a few PWA apps listed for download, but if core Windows 10 apps are retired, Microsoft could become one of the pioneers of this new push in a similar way it did with UWP back in 2015 Source: Microsoft Could Retire Several Windows 10 Apps
-
StressPaint malware is "developed professionally" and could be be harvesting accounts for anything from credential selling and identity theft, to malvertising and propaganda campaigns, warn researchers. Users who download a painting software advertised as a tool for stress relief might soon find themselves stressed out because the program is actually a front for malware which steals their Facebook credentials and payment information. 'StressPaint' first appeared a few days ago and at the time of writing has infected over 45,000 Facebook users. The attacks appear to specifically target users who operate Facebook pages and have configured a payment method into the account. Uncovered by Radware, the malware has quickly spread around the world with a high infection rate, indicating what researchers say "indicates this malware was developed professionally". It's also suggested that the attackers could go after Amazon users in a future campaign, given it has a dedicated section in a control panel used in the campaign which has been analysed by researchers. An infection campaign is carried out via phishing emails and users are socially engineered to believe they're visiting a real website - AOL is used as a hook in many of the attacks. However, the website they're being driven to is in fact a front for the malicious activity. The site promotes software called 'Relieve Stress Paint' and urges the user to download it for free. If they do download and run the file, a window opens to show a basic painting program to the user, to give the impression that nothing suspicious happening while the malware runs in the background. However, once 'Relieve Stress Paint' is launched, the malware immediately runs and drops files onto the system and it will look to steal information from that moment - then subsequently each time the computer is restarted. StressPaint steals information by copying the content of Chrome browser cookies and login date files. If saved Facebook credentials are found, they're sent to a C2 server. Once the stolen credentials are validated, additional information is collected on the compromised account, including the number of friends, whether the account manages a page or not, or if a payment method is connected to the account. "Security tools, like anti-virus or endpoint detection and response, always look for suspicious active processes on the system and general credential stealing methods like key logging or hooking," Adi Raff, security research team leader at Radware told ZDNet. "We believe that the process of the malware is only active on the system for less than a minute on specific occasions (like first run, computer restart and stress pain tool rerun) and that the data theft is done from a copy of Chrome files (cookies/login data) which helps the malware stay undetected". Currently, the attacks only appear to be collecting data, but researchers suggest the stolen information could be used for profit in a number of ways. They include selling the credentials on underground forums, extorting victims by threatening to reveal personal information, espionage, profit from stolen payment information and identity theft. However, it's suggested the fact the attackers are looking for accounts with pages and users with large amounts of friends means those behind the campaign - who've not been identified - are playing a long game. "With the stolen credentials, access to web pages and payment details, the group can launch malicious advertisement campaigns, whether to make profit or spread more malwares. They can use small amounts from each user without raising suspicion and collect a critical mass to launch any activity," warn researchers, who say the same applies to propaganda. "With the same information, instead of advertising a product or a service, they can run a campaign to promote their agenda and reveal people/personal identities." Radware has disclosed the research to Facebook. "We are investigating these malware findings and we are taking steps to help protect and notify those who are impacted," Pete Voss, Facebook communications manager told ZDNet. In order to avoid falling victim to a StressPaint attack, Radware urges users to be careful what they click. "To stay protected, people need to make sure that they are downloading applications from legitimate sites and always double check the site in the browser before downloading," said Raff. Source: This malware targets Facebook log-in details, infects over 45,000 in just days | ZDNet
-
Apps are also sharing data with third-party services The Google Play Store might be full of apps and games that are tracking children without the express permission from the parent, and Google doesn’t seem to be doing much about it. Following Facebook’s data leaking scandal with Cambridge Analitica, a lot of people have turned their attention to other social networks that might be doing the same thing. It turns out that we ought to be looking towards mobile apps as well, at least on Android, as a newly released study revealed. It’s one thing to track adults on Facebook or through other means, but tracking children it feels even more despicable. And the companies doing this actively have a very good reason for it, and it’s usually all about making money. Thousands of Android apps are tracking children According to Education Week, a study named “'Won't Somebody Think of the Children?' Examining COPPA Compliance at Scale” was published in the Proceedings on Privacy Enhancing Technologies journal. It underlines that a large number of Android apps might be violating the federal laws in the United States by tracking minors and gathering data without the express permission of their parents. COPPA stands for Children's Online Privacy Protection Act, and it’s supposed to protect children under the age of 13, and it refers specifically to gathering personal information without parental consent. What’s even worse is that there are literally thousands of such apps, with most of them still available for download today. The study covered 5,855 popular Android apps released between November 2016 and March 2018. The study uncovered some worrying facts. About 5% of the apps were gathering the user’s location and contact data (telephone number or email address), without any kind of parental consent. Another 1,100 apps, which made up about 19% of the total, were sharing sensitive information with third-parties, even if the terms of service prohibit such exchange. This type of data is used for behavioral advertising or targeted advertising. Ever wonder why your kid is getting ads for exactly the toy he wanted? 49% of the apps in the study (2,281) were actually in violation of the Google's terms of service, which prohibits sharing so-called persistent identifiers. It’s not personal information per say, but used in conjunction with other data and over long periods of time can be useful to determine a profile for the user. And, to make things even worse, of the 1,280 apps that were using Facebook integration, about 92% didn’t protect kids under 13 by using the proper configuration settings. It’s worse than you imagine The study only covered 5,800 apps release in a span of about two years, and that’s a mear pittance of the total number of apps in the store. Not to mention the fact that the researchers were only looking at the most popular apps. There are probably thousands more that might not be as popular, but they are possibly doing even more harm. And the real question is the following: What is Google doing to control this problem? The answer is probably not all that much. Source: Thousands of Android Apps Are Tracking Kids Without Parental Consent
-
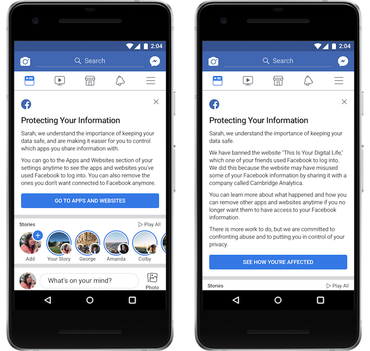
Here's how to check if you or a Facebook friend were connected to the "This is Your Digital Life" quiz, which is how Cambridge Analytica harvested data. Facebook has begun rolling out a feature to some users that will notify them if their data was accessed as part of the Cambridge Analytica data scandal. Facebook previously promised it will notify users whose data may have been utilized for political gain. Facebook users have started seeing one of two messages at the top of their News Feed -- both using the header Protecting Your Information. One message will focus on Cambridge Analytica, while the other focuses on general Facebook privacy, data, and app control. If you're waiting for Facebook's News Feed notification, you can visit this link to see if your information was shared. Up to 87 million Facebook users had their data improperly accessed, the social network has revealed. If you or a Facebook friend were connected to the "This is Your Digital Life" quiz, which is the source of Cambridge Analytica's data, you'll see this message at the top of your news feed: If your data wasn't accessed by Cambridge Analytica, Facebook will link to broader settings so you can protect your information on the social network and across its vast app ecosystem. It's been about a month since it was revealed Cambridge Analytica harvested information belonging to millions of Facebook users to determine how they may vote at the ballot box during US President Donald Trump's election campaign. The scandal has rocked Facebook's stock price and its trust with users. Facebook CEO Mark Zuckerberg is set to testify in front of congress this week to answer lawmakers' questions about the Cambridge Analytica scandal. He's repeatedly apologized for the scandal, and is promising more tools and transparency for Facebook users to protect their data. Facebook hasn't immediately responded to requests for comment on the rollout of the "This Is Your Digital Life" tool. Source: How to tell if Cambridge Analytica accessed your Facebook data | ZDNet
-
- 1
-

-

[Solved] Can't get rid of 'Nagware'
Starbuck replied to PEV's topic in Tech Support & Discussions Forum
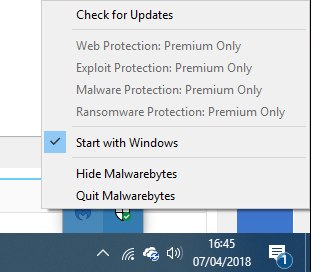
Hi Ray As Ken has already mentioned... this isn't the same message you had originally. This message is basically telling you that your version of MalwareBytes is now out of date and a new version is available. Latest version is 3.4.4 and was released on March 6th. Updating your version is the obvious answer. If you don't want to receive notifications of new versions ( not recommended ) you can turn off the notifications. Also, if you are running the free version of MalwareBytes.... there's no advantage in having it start with Windows. Right click on the Taskbar icon and click on 'Start with Windows', to remove the tick. -
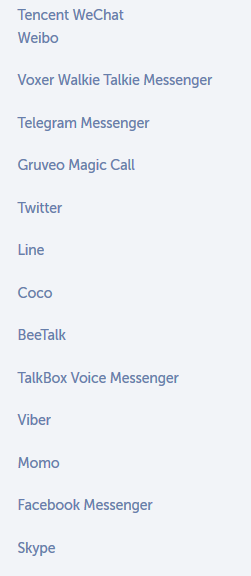
Security company warns of new Android malware in the wild Android devices are being targeted by a new form of malware that is specifically aimed at stealing private conversations on IM applications like Facebook Messenger, Skype, Telegram, Twitter, Viber, and others. The malware, which was detected by Trustlook (via FossBytes), has the capabilities to modify the “/system/etc/install-recovery.sh” file in order to start at every boot, thus making sure that it can extract instant messaging data even if the device is restarted. The first infected application is called Cloud Module and is spreading in China as package name com.android.boxa. It hasn’t yet reached the Google Play Store, and most likely the malware is supposed to target devices using non-store distribution tactics, such as email and downloads from third-party hosting sites. Chats uploaded to remote server In other words, Android users who only install apps from the Google Play store should be safe. While Android security solutions could detect the Trojan, Trustlook warns that the malware was designed to avoid detection, including anti-emulator and debugger detection techniques that make it possible to bypass dynamic analysis. “Code obfuscation/hiding increases the malware author’s ability to avoid detection and becomes a sophisticated challenge to anti-virus software,” Trustlook notes in its analysis Once the malware manages to compromise an Android device, it automatically looks for conversations in the said applications. The data is extracted and then sent to a remote server. The security vendor says the server’s IP address is mentioned in the malware configuration file, allowing the Trojan to operate without any further command send by the author. The full list of instant messaging apps that are being targeted by the malware is available below, and keep in mind that as long as you stick with legitimate download sources for Android apps, this new form of malware is highly unlikely to compromise your device. Also, if you’re running third-party security software, updating it should help block any possible intrusion. Source: New Android Virus Extracts Your Facebook, Skype, Telegram Messages
-
iPhone users are still vulnerable to being tricked into handing over passwords. Apple knows it — but won't do anything about it. iPhone or iPad users, if you update to iOS 11.3 now, you'll have new features and a bunch of security updates. But you'll still be just as vulnerable to on-device phishing attacks as you ever were. A long-expected privacy icon debuts in the software update out Thursday which help users identify when Apple requests more of their personal information. The update doesn't change how much data Apple collects, but it helps show what data will be collected when Apple apps and features are used for the first time. "You won't see this icon with every feature since Apple only collects this information when it's needed to enable features, to secure our services, or to personalize your experience," a screen says, once you update. Maybe the timing is a coincidence, but this seems like a way to grab some good headlines amid Facebook's recent data sharing controversy. Will Strafach, a security researcher with a focus on mobile, knows iOS better than most. He told ZDNet that the privacy icon will have some benefits. "Although the purpose was misinterpreted as some kind of indicator -- it is not -- the actual purpose of giving information on how data is used is a very good thing I believe," he said. "Many people these days wonder about how their data is used and just have no idea, so if Apple is going to ask for something sensitive, it seems very helpful to give information to the user on data management -- and users can then hold them to it instead of it being ambiguous." The downside is that, contrary to several reports, the privacy icon actually has nothing to do with preventing phishing attacks that try to steal your iCloud password. For its part, Apple never confirmed that the privacy icon would do anything of the sort. We reached out to Apple, but a spokesperson would not comment on the record. Although phishing attacks on the desktop have been around for years, they're less so targeted to the individual device. And as widely celebrated for their security as iPhones and iPads are, the device's weakest link is often a result of tricking the average user into turning over their password. It's a problem that Apple doesn't seem to want to tackle -- despite a rash of attention earlier this year, when Felix Krause demonstrated in a blog post how easy it was to trick an iPhone or iPad user into turning over their Apple ID credentials. In a proof-of-concept, he said users are "trained to just enter" their email address and password "whenever iOS prompts you to do so." Any long-term iPhone or iPad user can tell you that their phone or tablet will randomly prompt for your password, but often it's not clear why. And that's something attackers are keen to capitalize on. One report called the attack a "hacker's dream." "Showing a dialog that looks just like a system popup is super easy. There is no magic or secret code involved. It's literally the examples provided in the Apple docs, with a custom text," said Krause. He described it as "less than 30 lines of code" that every iOS engineer would know. Even with two-factor authentication, users aren't necessarily safe, said Krause. If you wanted to inflict damage, you only need a user's Apple ID email address and password to wipe a person's device without warning. Apple says in a developer post that it's difficult to combat phishing -- or social engineering as it's often referred to. Others say it's not that difficult. "I would like to see the password requests show up as a banner alert or notification sent by the Settings app, which should send the user to the Settings app when pressed in order to enter their credentials," said Strafach. "No icon or anything else is sufficient because the running app is able to mess with all user interface elements including status bar," he said. "Using an alert and redirect to Settings would completely solve the issue." It's a simple solution that Krause -- and others -- have already suggested. But Apple won't budge, and its customers remain at risk. Source: That new 'privacy icon' in iOS 11.3 does nothing to prevent password phishing
-
Monero-mining Android malware will exhaust your phone in its quest for cash. A new strain of Android malware will continuously use an infected device's CPU to mine the Monero cryptocurrency until the device is exhausted or even breaks down. Security company Trend Micro has named the malware HiddenMiner because of the techniques it uses to protect itself from discovery and removal. Like most cryptocurrency-mining software, HiddenMiner uses the device's CPU power to mine Monero. But Trend Micro said that because there is no switch, controller, or optimizer in HiddenMiner's code it will continuously mine Monero until the device's resources are exhausted. "Given HiddenMiner's nature, it could cause the affected device to overheat and potentially fail," the company said. If the researchers' concerns are correct, this is not the first cryptocurrency-mining malware to put your smartphone at risk: last year the Loapi Android malware worked a phone so hard that its battery swelled up and burst open the device's back cover, wrecking the handset within 48 hours. Trend Micro said the two pieces of malware share similarities, noting that Loapi's technique of locking the screen after revoking device administration permissions is analogous to HiddenMiner's. Researchers at the company identified the Monero mining pools and wallets connected to the malware, and spotted that one of its operators withdrew 26 XMR -- around $5,360 -- from one of the wallets. This, they said, indicates a "rather active" campaign of using infected devices to mine cryptocurrency. HiddenMiner poses as a legitimate Google Play update app, and forces users to activate it as a device administrator. It will persistently pop up until victims click the Activate button; once granted permission, HiddenMiner will start mining Monero in the background. It also attempts to hide itself on infected devices, for example by emptying the app label and using a transparent icon after installation. Once activated as device administrator, it will hide the app from the app launcher. The malware will hide itself and automatically run with device administrator permission until the next device boot. HiddenMiner also has anti-emulator capabilities to bypass detection and automated analysis. It's also hard to get rid of: users can't uninstall an active system admin package until device administrator privileges are removed first. But HiddenMiner locks the device's screen when a user wants to deactivate its device administrator privileges, taking advantage of a bug found in Android operating systems before Android 7.0 Nougat. Trend Micro said that HiddenMiner is found in third-party app marketplaces and is affecting users in India and China, but it won't be a surprise if it spreads beyond these countries. The emergence of this malware should reinforce the need for mobile security hygiene, said Trend Micro: download only from official app marketplaces; regularly update the device's OS, and be careful about the permissions you grant to applications. Source: Android security: This malware will mine cryptocurrency until your smartphone fails | ZDNet
-
The malware attempts to take your antivirus products out of the equation before locking systems. A new type of ransomware which tries to uninstall security software on victim PCs has been discovered in the wild. The ransomware, dubbed AVCrypt, was first discovered by MalwareHunterTeam and later analyzed by security professionals at Bleeping Computer. According to an analysis of the malware, AVCrypt will attempt to not only remove existing antivirus products before encrypting a compromised computer but will also delete a selection of Windows services. Researchers Lawrence Abrams and Michael Gillespie say that the ransomware "attempts to uninstall software in a way that we have not seen before," which marks the malware as unusual. The true purpose of the malware -- which appears to be ransomware due to its capabilities -- is also in question, as some elements appear unfinished. There are elements of encryption, but no true ransom note, and together with AVCrypt's process deleting, it is possible the malware may also be utilized as a wiper. It is not yet known how AVCrypt targets victims. However, when the malicious code executes on a victim's PC, the malware will first attempt to remove security software by targeting Windows Defender and Malwarebytes, or by specifically querying for other antivirus software before attempting to uninstall the programs. In order to eradicate AV products, the ransomware deletes Windows services which are required for the protective services to run properly, including MBAMProtection, Schedule, TermService, WPDBusEnum, WinDefend, and MBAMWebProtection. The malware then checks to see if any antivirus software is registered with the Windows Security Center and deletes these details through the command line. During tests, however, the researchers say that the malware was unable to delete Emisoft antivirus software through these techniques. Whether or not the deletion of Windows services to hamper AV protections would work with other solutions is unknown. The wiper features do not completely destroy Windows builds, but likely will cause service degradation. Once this stage is complete, AVCrypt then uploads an encryption key to a TOR location together with system information and timezone. The malware then scans for files to encrypt, renaming them in the process. The ransom note, saved as "+HOW_TO_UNLOCK.txt," does not contain any decryption instructions or contact information; instead, there is what appears to be placeholder "lol n" text. It appears that the ransomware is in development stages, and while there is a tenuous link between AVCrypt and a recent attack on a Japanese university, it is not known whether the malware was responsible. Microsoft told the publication that only two samples of this malware have been detected and so the company also believes that AVCrypt is not yet complete. "This ransomware is quite destructive to an infected computer, yet at the same time does appear to upload the encryption key to a remote server," the researchers say. "Therefore, it is not known whether this is a true ransomware or a wiper disguised as one." Source: AVCrypt ransomware attempts to eradicate your antivirus | ZDNet
-
Dang! Don’t you just hate it when you search for Amazon on Google, you click on the top link (which of course must be legit, right? – it’s from Google!) and then you somehow wind up infected with “Malicious Pornographic Spyware” with a dab of “riskware” on top? Yep, not for the first time, Google’s been snookered into serving a scam tech support ad posing as an Amazon ad. This is déjà vu. Thirteen unlucky months ago, scammers slipped a fake Amazon ad under Google’s nose. Anybody who clicked on it was whisked to a Windows support scam. ZDNet reported on that one in February 2017, and it brings us news of the bad ad rebirth once again. On Friday, ZDNet’s Zack Whittaker reported that for hours on Thursday, the top Google search result for “Amazon” was pointing to a scam site. Top, as in, it outranked even the legitimate search result for Amazon.com. Users who clicked on the bad ad were whisked to a page that tried to terrify them with reports of malware infection so they’d call a number for “help.” The ad masqueraded as an official Apple or Windows support page, depending on the type of computer in use. Then, just as fake tech support ads tend to do, and just as the fake Amazon ad did last February, the bad ad shrugged off users’ attempts to dismiss a popup box that warned them about malicious pornographic spyware and riskware etc. (What IS “pornographic spyware?” Spyware accompanied by heavy breathing?). According to ZDNet’s analysis of the code, trying to close the popup would have likely triggered the browser to expand and fill up the entire screen, making it look like a system had been grabbed by ransomware. ZDNet says it appeared through a proxy script on a malicious domain to make it look as though the link fully resolved to an Amazon.com page, “likely in an effort to circumvent Google’s systems from flagging the ad.” The malicious domain was registered by GoDaddy, and the apparent domain owner didn’t respond to ZDNet’s inquiries. A spokesperson for Google told ZDNet that the company doesn’t tolerate advertising of illegal activity and takes “immediate action to disable the offending sources” when it finds ads that violate its policies. GoDaddy pulled the site offline within an hour of being contacted by ZDNet. A GoDaddy spokesperson said that its security team found that the ad violated its terms of services, so they removed it. Google’s swimming in these bad ads. Last week, it announced that in 2017, it took down more than 3.2 billion that violated advertising policies. That’s an average of 100 per second, Google said, and it’s up from 1.7 billion removals of bad ads in the prior year. Google also booted 320,000 online publishers off for violations like showing Google-supplied ads alongside inappropriate or controversial content, according to Scott Spencer, Google’s director of sustainable ads. What to do? Google’s working hard to kill bad ads, but they’re obviously still getting through, including those that contain malware. So to help you stay vigilant, here are some suggestions on what to do if you get hit with one of these fake tech support scams, be it on the phone or as “Riskware! Spyware!” taking over your browser: If you receive a cold call about accepting support, just hang up. If you receive a web popup or ad urging you to call for support, ignore it. If you need help with your computer, ask someone whom you know and trust. When searching for Amazon, remember that you don’t need to use Google. Simply go straight to Amazon.com. Source: Fake Amazon ad ranks top on Google search results
-
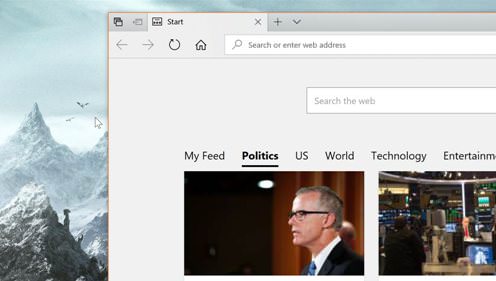
All links in the Windows 10 mail client will open in Edge Microsoft is about to make another highly-controversial change in Windows 10, and without a doubt, many users won’t be happy with it. The company is thinking of forcing users to open links in the Mail app in Microsoft Edge exclusively starting with the Redstone 5 update. A change included in the latest Windows 10 Redstone 5 preview build reveals that clicking links in the Mail app will launch Edge instead of whatever browser you are using as default. Even if Google Chrome or Mozilla Firefox is installed and used as your daily driver, this new behavior makes Windows 10 ignore your settings and use Edge exclusively. Microsoft says users can only benefit from this change because Edge is the most secure and battery-friendly browser currently on the market. “For Windows Insiders in the Skip Ahead ring, we will begin testing a change where links clicked on within the Windows Mail app will open in Microsoft Edge, which provides the best, most secure and consistent experience on Windows 10 and across your devices,” the firm explains. “With built-in features for reading, note-taking, Cortana integration, and easy access to services such as SharePoint and OneDrive, Microsoft Edge enables you to be more productive, organized and creative without sacrificing your battery life or security.” Still waiting for feedback On the good side, Microsoft says it’s looking for feedback from Windows insiders, so no decision has been made just yet. For those of you who are already using Edge as the default browser, this change won’t have any impact. Statistics, however, show that Edge is being used as the main browser only on a small number of PCs. Google Chrome leads in terms of global share with more than 60 percent, while Edge is far behind with some 5 percent. Redstone 5 is projected to launch in the fall, so Microsoft still has enough time to abandon what’s very likely to become a very criticized strategy. Source: Microsoft Wants to Force Edge on Windows 10 Users in the Worst Possible Way